
General Router FAQ
VPN Passthrough

|
General Router FAQVPN Passthrough |

|
This applies to NAT mode only. If you have a VPN server running behind the Vigor router (as opposed to using the Vigor's own VPN facilities) you can set the router to pass through to it. This will work for PPTP, L2TP IPSec+ESP protocols; it will not work for IPSec+AH mode because the AH protocol is designed to block address translation (due to embedding the source IP addresses in the header).
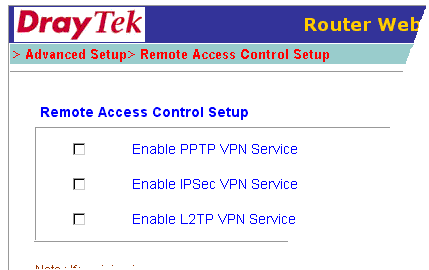
You must firstly disable the router's own VPN facility, otherwise it will intercept the VPN traffic :
The PPTP protocol uses TCP Port 1723 for link setup, and IPSec/ESP uses Port500 for IKE setup. If you enable those ports in the router's open port setup, the router will automatically also open up the corresponding VPN protocol, i.e. GRE or ESP respectively.
The screenshot below shows this method for the IPSec or PPTP protocols:
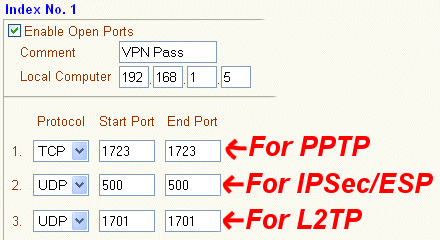
You do not need to set all of those rules above - select whichever of PPTP, IPSec or L2TP you are using (you can use all of them).
If the above method does not work for your particular server protocols you can instead enable the router's DMZ facility to expose the VPN server to the outside world; this is less secure than opening just the required ports/protocols (as above). Tpasshe DMZ should point to the internal IP address of the router : 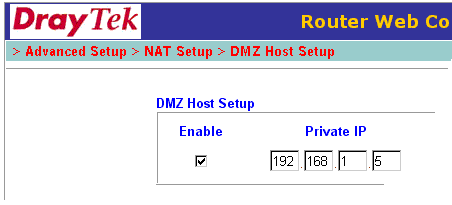
If you want to run a VPN client behind the Vigor, then depending on the protocol, it may work without any specific settings being required on the Vigor; try it first. You will probably still need to disable the router's own VPN function, as above, and in some circumstances use the DMZ, also as above.
IPSec passthrough is disabled by default on the Vigor2820. The reason for this is because IPSec passthrough is not compatible with the new NAT-T support of the routers internal VPN server. The Vigor2820 NAT-T support allows remote VPN clients that are behind a NAT router to more easily connect via VPN.
There is a telnet command to enable IPSEC passthrough. The command is srv nat ipsecpass on.
VPN passthrough is where a client or server behind the Vigor is generating the tunnel endpoint itself, rather than the router itself is creating the tunnel. A VPN server behind the Vigor can accept many different remote clients creating VPN tunnel to it. You can also have mutiple VPN clients behind the router each making a tunnel to a different remote VPN server.
You cannot have more than one VPN client behind the Vigor creating a tunnel to the same remote VPN server. This is because the VPN protocol reply packets are indistinguishable from each other, so the router cannot tell which VPN client the reply packets are intended for, if they come from the same remote host. If this is required, then consider letting the Vigor create the tunnel itself (instead of passthrough) and then multiple clients can then pass through that one tunnel, which is also more efficient. You can run multiple internal (LAN-side) VPN clients if they each connecting to a different remote server.
NOTICE : This document is © SEG Communications and may not be distributed without specific written consent. Information and products subject to change at any time without notice.