DrayTek UK Users' Community Forum
Help, Advice and Solutions from DrayTek Users
2960 - various issues and UI ambiguities
- peter-h
- Topic Author
- Offline
- Junior Member
-

Less
More
- Posts: 82
- Thank you received: 0
24 Feb 2020 17:42 #1
by peter-h
2960 - various issues and UI ambiguities was created by peter-h
For years I had two sites each with a 2955, working faultlessly. Well, we knew the 2955 had loads of bugs e.g.
- remote admin always open; solution is to port forward 443 to an unused internal IP
- port 161 packets bypass the firewall totally; same solution
- obscure issues with MTU negotiation not working
- VPN traffic bypasses the firewall
We then discovered a mysterious problem when we got VOIP phones. It turned out there is a bug in the 2955 whereby it gets into a state every few mins and dumps outgoing UDP for ~10 secs (symptom is like the phone mike going dead) and then it works again, for a bit. We did have the whole DOS attack protection feature turned off since that could do it; it doesn't work properly anyway.
So we bought a 2960 because it is more recent and the release notes refer to the above (1st two) bugs, in the hope it fixes the VOIP loss also, and it does.
It is a lot more powerful box than the 2955 but the UI is weird in places. Well, the 2955 had badly laid out forms with parameters which nobody knew what they did but mostly you followed Mikey's Guides and left the defaults, and it worked. The 2960 has some strange stuff e.g.
- dial-in VPNs (called Teleworker on the old boxes) are configured entirely
- the section VPN and Remote Access / VPN Profiles shows six tabs
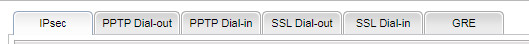
on which the two PPTP ones do absolutely nothing useful; whatever you config there seems to do nothing. Well, unless the whole VPN and Remote Access section is actually just for site-site
- in places there is a config for L2TP over IPSEC but elsewhere it says Avoid L2TP with IPSEC!
- remote admin always open; solution is to port forward 443 to an unused internal IP
- port 161 packets bypass the firewall totally; same solution
- obscure issues with MTU negotiation not working
- VPN traffic bypasses the firewall
We then discovered a mysterious problem when we got VOIP phones. It turned out there is a bug in the 2955 whereby it gets into a state every few mins and dumps outgoing UDP for ~10 secs (symptom is like the phone mike going dead) and then it works again, for a bit. We did have the whole DOS attack protection feature turned off since that could do it; it doesn't work properly anyway.
So we bought a 2960 because it is more recent and the release notes refer to the above (1st two) bugs, in the hope it fixes the VOIP loss also, and it does.
It is a lot more powerful box than the 2955 but the UI is weird in places. Well, the 2955 had badly laid out forms with parameters which nobody knew what they did but mostly you followed Mikey's Guides and left the defaults, and it worked. The 2960 has some strange stuff e.g.
- dial-in VPNs (called Teleworker on the old boxes) are configured entirely
- the section VPN and Remote Access / VPN Profiles shows six tabs

on which the two PPTP ones do absolutely nothing useful; whatever you config there seems to do nothing. Well, unless the whole VPN and Remote Access section is actually just for site-site
- in places there is a config for L2TP over IPSEC but elsewhere it says Avoid L2TP with IPSEC!
Please Log in or Create an account to join the conversation.
- peter-h
- Topic Author
- Offline
- Junior Member
-

Less
More
- Posts: 82
- Thank you received: 0
24 Feb 2020 17:49 #2
by peter-h
Replied by peter-h on topic Re: 2960 - various issues and UI ambiguities
(remainder of post due to 3000 char limit)
- there are lots of subtle differences 2955 to 2960 in the routing behaviour and especially the firewall behaviour. For example if you had an internal LAN 192.168.1.* and a 2nd subnet with a public IP of 100.101.102.103-105, you could access a device on .103 from a PC on the local LAN. That device would not be presented with the IP of that PC; the packets would go outside and back in and would appear as coming in from your public IP. On the 2960 they appear as coming from the PC's internal address e.g. 192.168.1.30 and if your .103 device is firewalled to reject packets from the open internet from 192.168.* (a good practice perhaps) then it is inaccessible, and there seems to be nothing that can be done in the firewall or anywhere else to fix this.
- on the site-site VPN config form, both the LAN IPs must end with 0
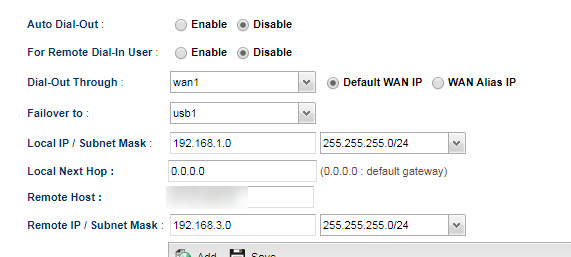
If you end with a .1 (as recommended by many guides from Draytek) it doesn't work. You can still connect the VPN manually (under Connection Management) but the auto packet trigger won't work and you get a syslog error pluto[8979]: ignoring duplicate netlink acquire event for 192.168.1.xx to 192.168.3.xx. On the 2955 it doesn't matter if you end the IPs with .0 or .1.
- the L2TP teleworker VPN does not work with android; the 2955 one did. It works ok with a win10 (native OS built-in client). PPTP works OK still.
- a teleworker client gets onto the internal LAN but gets no internet access. You have to create a firewall rule like this (here we have two teleworkers, one pptp and one l2tp)
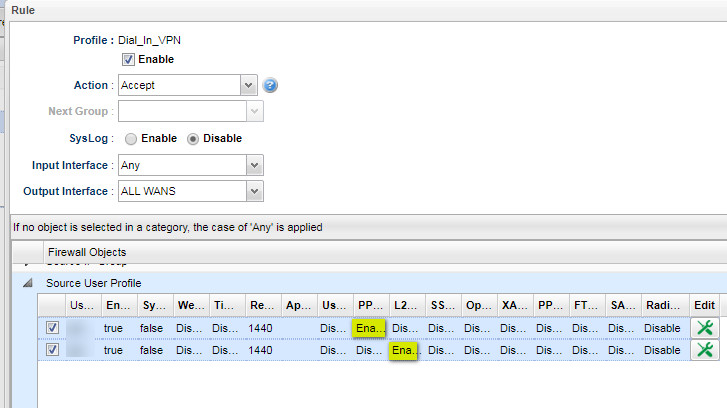
On the 2955, this "just worked", even though in both router types the default firewall mode was Block.
- there are no doubt many other things like this
Draytek need to product much better documentation and user examples. At £400 these are not cheap boxes.
- there are lots of subtle differences 2955 to 2960 in the routing behaviour and especially the firewall behaviour. For example if you had an internal LAN 192.168.1.* and a 2nd subnet with a public IP of 100.101.102.103-105, you could access a device on .103 from a PC on the local LAN. That device would not be presented with the IP of that PC; the packets would go outside and back in and would appear as coming in from your public IP. On the 2960 they appear as coming from the PC's internal address e.g. 192.168.1.30 and if your .103 device is firewalled to reject packets from the open internet from 192.168.* (a good practice perhaps) then it is inaccessible, and there seems to be nothing that can be done in the firewall or anywhere else to fix this.
- on the site-site VPN config form, both the LAN IPs must end with 0

If you end with a .1 (as recommended by many guides from Draytek) it doesn't work. You can still connect the VPN manually (under Connection Management) but the auto packet trigger won't work and you get a syslog error pluto[8979]: ignoring duplicate netlink acquire event for 192.168.1.xx to 192.168.3.xx. On the 2955 it doesn't matter if you end the IPs with .0 or .1.
- the L2TP teleworker VPN does not work with android; the 2955 one did. It works ok with a win10 (native OS built-in client). PPTP works OK still.
- a teleworker client gets onto the internal LAN but gets no internet access. You have to create a firewall rule like this (here we have two teleworkers, one pptp and one l2tp)

On the 2955, this "just worked", even though in both router types the default firewall mode was Block.
- there are no doubt many other things like this
Draytek need to product much better documentation and user examples. At £400 these are not cheap boxes.
Please Log in or Create an account to join the conversation.
- admin2
- Site Admin
-

Less
More
25 Feb 2020 16:47 #3
by admin2
The performance of IPSEC with Xauth or SSL VPN is much better than that of L2TP over IPSEC. One of the reasons of using L2TP was having a username / password for auth in addition to IPSEC (IPSEC without L2TP is still extremely secure if configured correctly) which is what Xauth provides as an alternative.
If you're able to do using the SmartVPN client should be a nicer experience for users. There are Windows, iOS and Android versions. I'd also try to use SSL instead of PPTP.
Yes, I agree if this was done all over again, the teleworker section should on balance have been similar to the 2955. I believe historically it was due to it following the format of the 3300V and it was a choice of making it similar to the 3300V which was the product the 3900 / 2960 were superseding, and so familiar to those users, or making it simlar to the other series.
Replied by admin2 on topic Re: 2960 - various issues and UI ambiguities
peter-h wrote:
but elsewhere it says Avoid L2TP with IPSEC!
The performance of IPSEC with Xauth or SSL VPN is much better than that of L2TP over IPSEC. One of the reasons of using L2TP was having a username / password for auth in addition to IPSEC (IPSEC without L2TP is still extremely secure if configured correctly) which is what Xauth provides as an alternative.
peter-h wrote:
L2TP teleworker VPN does not work with android
If you're able to do using the SmartVPN client should be a nicer experience for users. There are Windows, iOS and Android versions. I'd also try to use SSL instead of PPTP.
peter-h wrote:
This is totally weird; there should be a Teleworker or similar section, and by all means reference a username from User Management in there
Yes, I agree if this was done all over again, the teleworker section should on balance have been similar to the 2955. I believe historically it was due to it following the format of the 3300V and it was a choice of making it similar to the 3300V which was the product the 3900 / 2960 were superseding, and so familiar to those users, or making it simlar to the other series.
Please Log in or Create an account to join the conversation.
- peter-h
- Topic Author
- Offline
- Junior Member
-

Less
More
- Posts: 82
- Thank you received: 0
26 Feb 2020 14:27 #4
by peter-h
Replied by peter-h on topic Re: 2960 - various issues and UI ambiguities
Is there a guide for Android and the 2960? I can find only this
https://www.draytek.com/support/knowledge-base/5276
and that is for the old routers.
A few hours later I can't get it to work. It gets part way, with syslog showing
"initial Main Mode message received on [IP]:500 but no connection has been authorised"
EDIT: I found the Linux version and it now connects, but as is the default case with the 2960 (but not the 2955) the client gets no internet access. The fix I posted previously for that doesn't work. Presumably the IPSEC traffic is treated differently by the router (for the purpose of routing requests to external IPs to the WAN) to the PPTP VPN. What sort of fw rule should be used to allow the dial-in user to go out of the WAN interface?
What I eventually did was abandoned IPSEC dial-in. It cannot work on windows because there is no native client, and while it connects on android (xauth) the 2960 does not give the client internet access. Nobody seems to know how to do this. I solved that on PPTP and L2TP over IPSEC dial-ins with a firewall rule.
and that is for the old routers.
A few hours later I can't get it to work. It gets part way, with syslog showing
"initial Main Mode message received on [IP]:500 but no connection has been authorised"
EDIT: I found the Linux version and it now connects, but as is the default case with the 2960 (but not the 2955) the client gets no internet access. The fix I posted previously for that doesn't work. Presumably the IPSEC traffic is treated differently by the router (for the purpose of routing requests to external IPs to the WAN) to the PPTP VPN. What sort of fw rule should be used to allow the dial-in user to go out of the WAN interface?
What I eventually did was abandoned IPSEC dial-in. It cannot work on windows because there is no native client, and while it connects on android (xauth) the 2960 does not give the client internet access. Nobody seems to know how to do this. I solved that on PPTP and L2TP over IPSEC dial-ins with a firewall rule.
Please Log in or Create an account to join the conversation.
Copyright © 2024 DrayTek


