DrayTek UK Users' Community Forum
Help, Advice and Solutions from DrayTek Users
Draytek 2955 - L2TP vulnerability causing reboots?
- peter-h
- Topic Author
- Offline
- Junior Member
-

Less
More
- Posts: 60
- Thank you received: 0
15 Nov 2018 08:00 #93369
by peter-h
Replied by peter-h on topic Re: Draytek 2955 - L2TP vulnerability causing reboots?
A good find 
Also you would need to be able to specify an IP range (or a subnet mask) because this well known hacker uses a range of IPs.
This is him
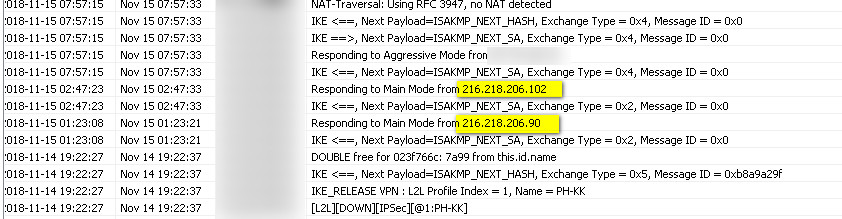
I can't tell how far he is getting, from this. Is "IKE" always IPSEC? That is used in L2TP (which I have enabled again, to see if the reboots return, and they have) and in the IPSEC site-site VPN. I could config the site-site one to accept connections only from the caller IP.
This is him hacking my home 2955, also at night as usual
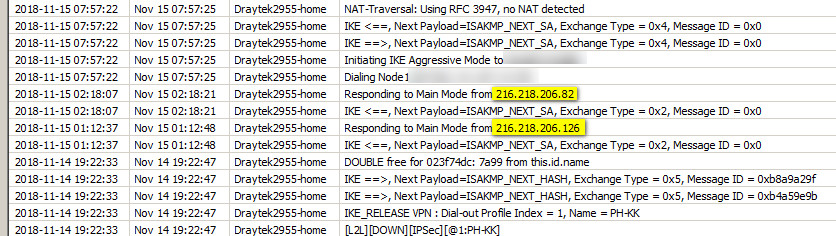
I have not been able to tie up reboot times with this hacker though. The syslog messages I saw around then, which I will post next time, indicate that the router may be rebooting due to an incoming VPN call not being able to be tied up to any VPN profile.
A pity Draytek have gone silent on the post-crash memory location data I sent them. They must know what is causing this.
What is "main mode"?
Based on this
https://www.draytek.com/en/faq/faq-vpn/vpn.others/why-the-vpn-connection-cannot-be-established/
it looks like no successful key exchange is being achieved, because both incomings from those IPs result in a left pointing arrow only.. I wonder if he is hacking the site-site VPN or the L2TP VPN? Edit: it must be L2TP because the site-site VPN is set to Aggressive Mode. On the teleworker VPNs there is no setting for Main or Aggressive.
Also you would need to be able to specify an IP range (or a subnet mask) because this well known hacker uses a range of IPs.
This is him

I can't tell how far he is getting, from this. Is "IKE" always IPSEC? That is used in L2TP (which I have enabled again, to see if the reboots return, and they have) and in the IPSEC site-site VPN. I could config the site-site one to accept connections only from the caller IP.
This is him hacking my home 2955, also at night as usual

I have not been able to tie up reboot times with this hacker though. The syslog messages I saw around then, which I will post next time, indicate that the router may be rebooting due to an incoming VPN call not being able to be tied up to any VPN profile.
A pity Draytek have gone silent on the post-crash memory location data I sent them. They must know what is causing this.
What is "main mode"?
Based on this
it looks like no successful key exchange is being achieved, because both incomings from those IPs result in a left pointing arrow only.. I wonder if he is hacking the site-site VPN or the L2TP VPN? Edit: it must be L2TP because the site-site VPN is set to Aggressive Mode. On the teleworker VPNs there is no setting for Main or Aggressive.
Please Log in or Create an account to join the conversation.
- hornbyp
- Offline
- Big Contributor
-

Less
More
- Posts: 1323
- Thank you received: 0
15 Nov 2018 14:31 #93375
by hornbyp
The description
here
sounds reasonable ...
There's an interesting phrase on that web page :-
Which I assume is the reason that the latest version of the Greenbow client, will no longer connect to the 2830
(I recently converted my web site - such as it is - to use HTTPS. It turned out that just enabling HTTPS wasn't enough for Google Chrome to declare it 'secure'. I had to jump through all sorts of hoops rearranging the order of the cipher algorthims and deleting others. I hadn't realised that this was even possible ... I naively thought these things were all standards-based and pre-ordained. Clearly not!
As an aside, don't forget that with L2TP/IPSec, the IPSec part is established first and L2TP happens over that IPSec connection. You probably already knew that, but worth saying out loud anyway
I've not tried it, but I bet it's possible for the Vigor to match the IPSec key
Replied by hornbyp on topic Re: Draytek 2955 - L2TP vulnerability causing reboots?
What is "main mode"?peter-h wrote:
The description
There's an interesting phrase on that web page :-
The first exchange between nodes establishes the basic security policy; the initiatorCisco wrote:
proposes the encryption and authentication algorithms it is willing to use.
Which I assume is the reason that the latest version of the Greenbow client, will no longer connect to the 2830
(I recently converted my web site - such as it is - to use HTTPS. It turned out that just enabling HTTPS wasn't enough for Google Chrome to declare it 'secure'. I had to jump through all sorts of hoops rearranging the order of the cipher algorthims and deleting others. I hadn't realised that this was even possible ... I naively thought these things were all standards-based and pre-ordained. Clearly not!
As an aside, don't forget that with L2TP/IPSec, the IPSec part is established first and L2TP happens over that IPSec connection. You probably already knew that, but worth saying out loud anyway
I've not tried it, but I bet it's possible for the Vigor to match the IPSec key
Please Log in or Create an account to join the conversation.
- hornbyp
- Offline
- Big Contributor
-

Less
More
- Posts: 1323
- Thank you received: 0
15 Nov 2018 16:32 #93378
by hornbyp
I'm losing my marbles:oops: ... I have :?
Android 8.0 Aggressive Mode L2TP/IPSec PSK
Replied by hornbyp on topic Re: Draytek 2955 - L2TP vulnerability causing reboots?
I've not tried it, but I bet it's possible for the Vigor to match the IPSec keyI wrote:
from one Dial-in User Profile and the L2TP credentials from another; It's definitely possible when using certificates.
I'm losing my marbles
Android 8.0 Aggressive Mode L2TP/IPSec PSK
Code:
16:01:54 Responding to Aggressive Mode from 82.132.244.67
16:01:54 Find Phase1 proposal: SHA2_256
16:01:54 Find Phase1 proposal: SHA2_256
16:01:54 Accept Phase1 prorosals : ENCR OAKLEY_AES_CBC, HASH OAKLEY_SHA
16:01:57 IKE <==, Next Payload=ISAKMP_NEXT_SA, Exchange Type = 0x4, Message ID = 0x0
It repeats a few times, but proceeds no further. Please Log in or Create an account to join the conversation.
- peter-h
- Topic Author
- Offline
- Junior Member
-

Less
More
- Posts: 60
- Thank you received: 0
15 Nov 2018 17:09 #93379
by peter-h
Replied by peter-h on topic Re: Draytek 2955 - L2TP vulnerability causing reboots?
How do you enable Aggressive mode on a teleworker VPN? I see no such config in the 2955. I do see that config option in the global IPSEC config...
I have just done an L2TP dial-in from Vodafone 4G (that's the IP you see below) using an android 6.0 phone (Samsung S7), and I get this
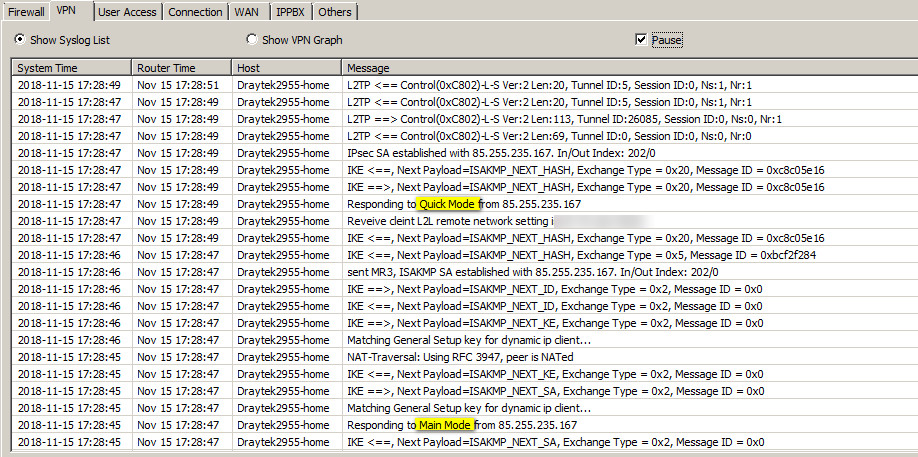
I have just done an L2TP dial-in from Vodafone 4G (that's the IP you see below) using an android 6.0 phone (Samsung S7), and I get this

Please Log in or Create an account to join the conversation.
- hornbyp
- Offline
- Big Contributor
-

Less
More
- Posts: 1323
- Thank you received: 0
15 Nov 2018 18:49 #93380
by hornbyp
The choice of mode is done at the client end. The Android client (at least on my Huawei P9) uses Main Mode, unless you put 'something' in the"IPSEC Secret (Not Used)" field. (I don't understand how Main Mode works in this scenario, because all the documentation says you need a fixed IP address).
When you trigger Aggressive Mode for a site-to-site VPN, the Vigor starts matching Keys in the Site-to-Site VPN Profiles, instead of the Global Key. I would
Replied by hornbyp on topic Re: Draytek 2955 - L2TP vulnerability causing reboots?
How do you enable Aggressive mode on a teleworker VPN? I see no such config in the 2955. I do see that config option in the global IPSEC config...peter-h wrote:
The choice of mode is done at the client end. The Android client (at least on my Huawei P9) uses Main Mode, unless you put 'something' in the"IPSEC Secret (Not Used)" field. (I don't understand how Main Mode works in this scenario, because all the documentation says you need a fixed IP address).
When you trigger Aggressive Mode for a site-to-site VPN, the Vigor starts matching Keys in the Site-to-Site VPN Profiles, instead of the Global Key. I would
Please Log in or Create an account to join the conversation.
- peter-h
- Topic Author
- Offline
- Junior Member
-

Less
More
- Posts: 60
- Thank you received: 0
15 Nov 2018 19:38 #93381
by peter-h
Replied by peter-h on topic Re: Draytek 2955 - L2TP vulnerability causing reboots?
Does the global key do anything then? It would be weird to take note of the Main v. Aggressive mode config in the global IPSEC config, while ignoring the shared key which is entered in the same box.
Please Log in or Create an account to join the conversation.
Moderators: Chris, Sami
Copyright © 2024 DrayTek


